DNS Firewall: First layer of protection from Phishing and Malware
If you are connected to the network of the University of Bern (e.g., via VPN, WiFi, or cable), the DNS Firewall offers you invisible protection against phishing and malware. We explain how the DNS Firewall works, what benefits it brings to you, and where the limits are.

The most important in a nutshell
The DNS Firewall is a security feature that is activated on the central DNS servers of the University of Bern and provides additional protection against phishing and malware.
When you call up a website from within the network of the University of Bern, the DNS Firewall checks whether the desired website contains any risks. In case of danger, you will be shown an information page instead of the desired website.
For the DNS Firewall to work, you must be connected to the network of the University of Bern (e.g., via WiFi, VPN, or cable) and use the central DNS servers (ns1.unibe.ch and ns2.unibe.ch), or be connected to the campus directory.
It is important to keep in mind that the DNS Firewall does not prevent the receipt of phishing emails, and in the case of new and targeted phishing websites, it may take some time for the protection to be effective. Therefore, despite DNS Firewall, it is important to be attentive and cautious.
What is the Domain Name System, or DNS for short?
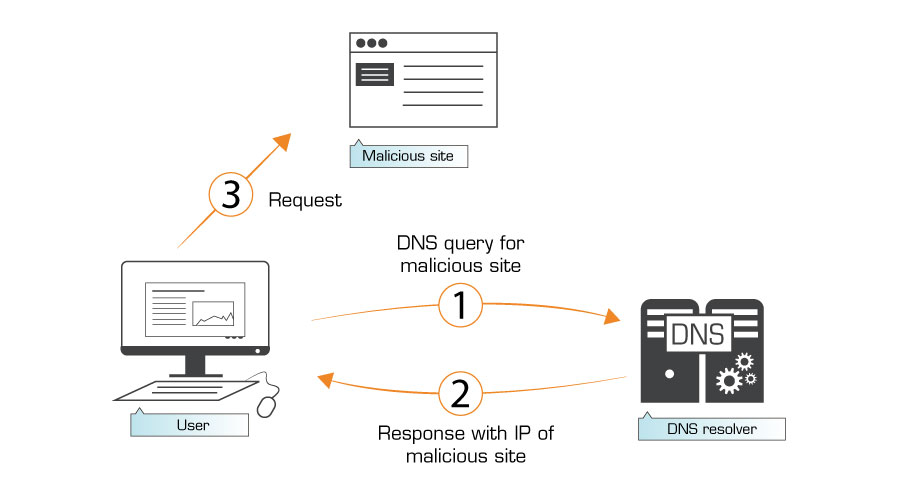
Every website on the Internet has two addresses under which it can be found, but only one of them can be easily remembered. For example, if we want to access the website of the University of Bern, we enter the domain name www.unibe.ch in the address bar of the web browser. Alternatively, we could enter 130.92.250.6 or 2001:620:400:2500::6.
The last two addresses are IP addresses (IP stands for Internet Protocol), and in fact, the web browser actually only works with these addresses. The Domain Name System, or DNS for short, converts the domain names into the corresponding IP addresses and thus forms the basis to use easily remembered domain names.
Converting domain names into IP addresses (and vice versa) is called DNS query or DNS resolution.
How does the DNS Firewall work?
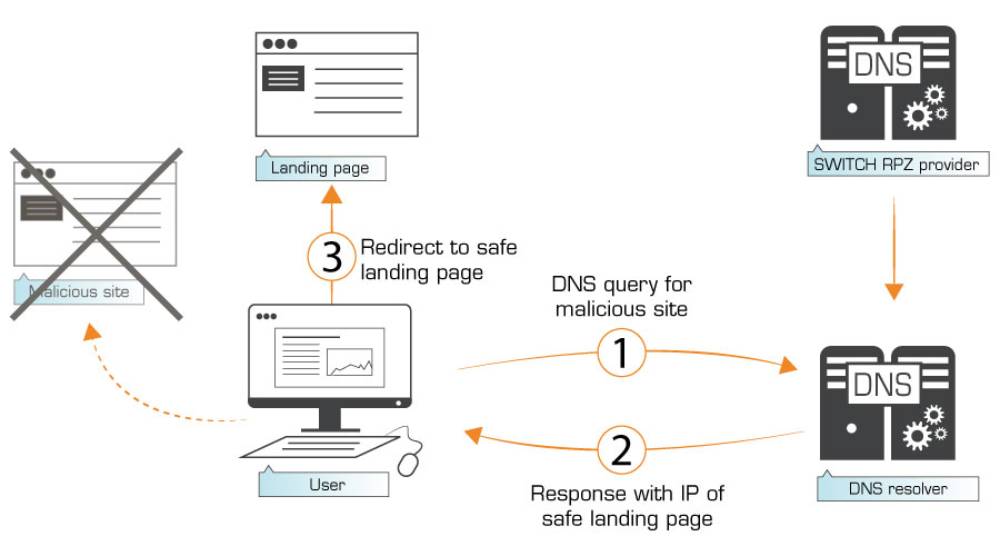
The DNS Firewall is part of the Domain Name System and checks with every conversion from domain name to IP address whether the domain name and thus the website has been classified as dangerous (e.g., phishing website or website contaminated with malware). Depending on the result of the check, a different IP address is returned to the web browser.
If everything is fine, the correct IP address is returned, and the desired web page is displayed. Otherwise, the IP address of an information page is returned to the web browser, and it is displayed instead of the correct web page.
In this way, a safe web page is always displayed. Either the requested one or the information page that was not the one that was expected but is not a fraudulent phishing website or a website contaminated with malware.
The DNS Firewall uses databases as a source of data. Thus, the desired website is not actively checked with every DNS query but only checked in the databases to see whether an entry exists.
Opening a website without DNS Firewall
Opening a website with DNS Firewall
What benefit do I get from the DNS Firewall?
For phishing and malware to work, they usually rely on an Internet connection and the Domain Name System. If you click on a link in a phishing email, a DNS query is made before the fraudulent website is displayed, and in the case of malware, the Domain Name System is needed for communication between the attacker and the malware (keyword: botnet).
By redirecting phishing links to a secure information page and preventing malware from phoning home, the DNS Firewall benefits from an additional protection mechanism that intervenes if one has accidentally clicked on a dangerous link or caught malware.
When is the DNS Firewall active?
To benefit from the protection provided by the DNS Firewall, you must be connected to the network of the University of Bern (e.g., via WiFi, VPN, or cable) and use the central DNS servers of the university or be connected to the campus directory. Normally, computers and smartphones are automatically configured correctly when connected to WiFi (eduroam or public-unibe) and when using a VPN. The technical staff of the institutes does the configuration of the computers at the workplace.
If you manage the DNS settings of your devices yourself, then as long as you are connected to the network of the University of Bern, you must use the DNS servers of the University of Bern. Information on how to configure the DNS settings can be found in the Service Portal.
How do I know that DNS Firewall has protected me?
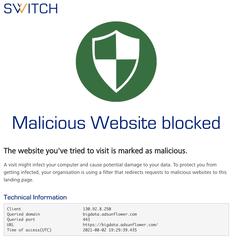
The main identifying characteristic is the information page displayed to you if you clicked on a link in a phishing email or tried to visit a malware-infected website. When you see the following web page, you know two things:
- Something is wrong with the link you clicked or the website you tried to visit, and
- the DNS Firewall has saved you from harm.
Normally, after you see the DNS Firewall information page, you can continue working as usual, and there is no need to take any action. If you are not sure or feel more comfortable, then, in any case, you can contact the technical officer(s) of your institute, run an antivirus scan, and/or change the password of the affected user account.
Certificate warning when displaying the information page
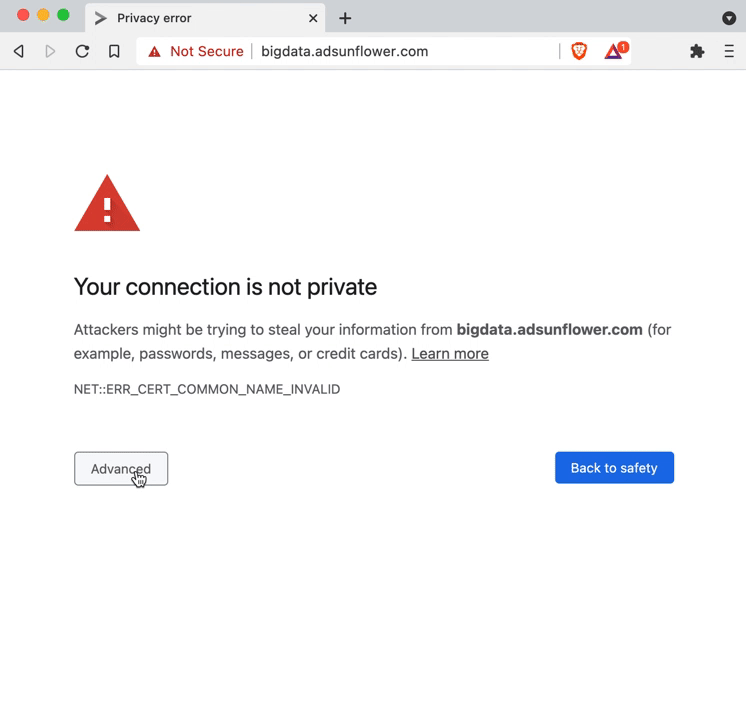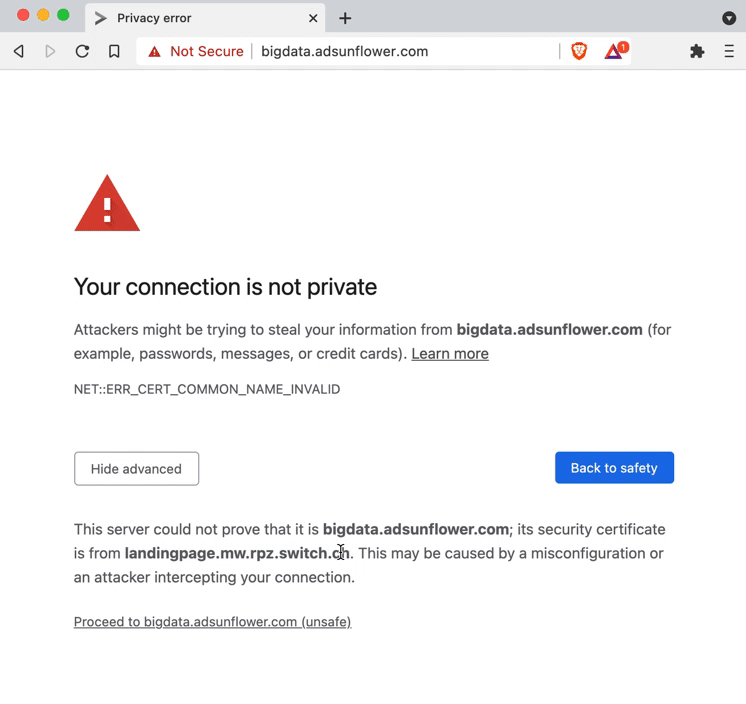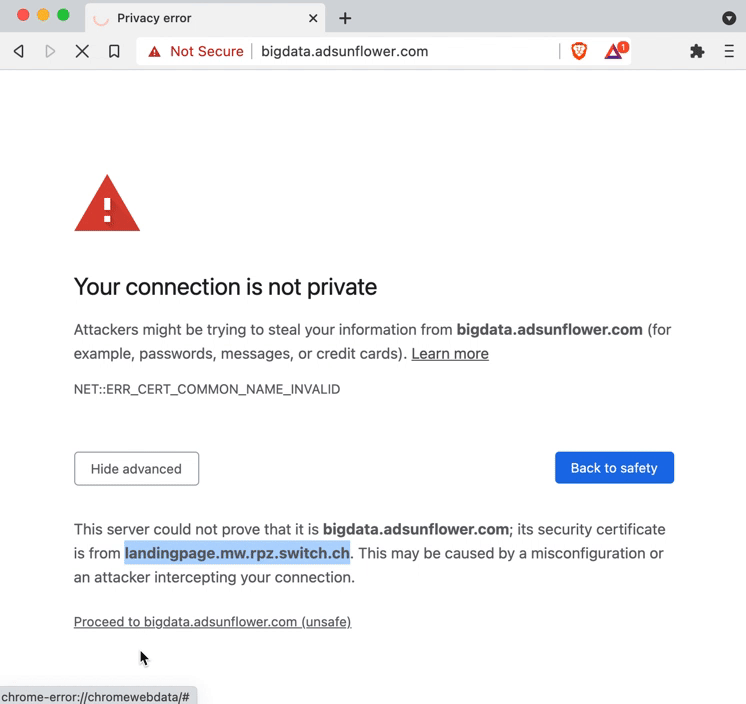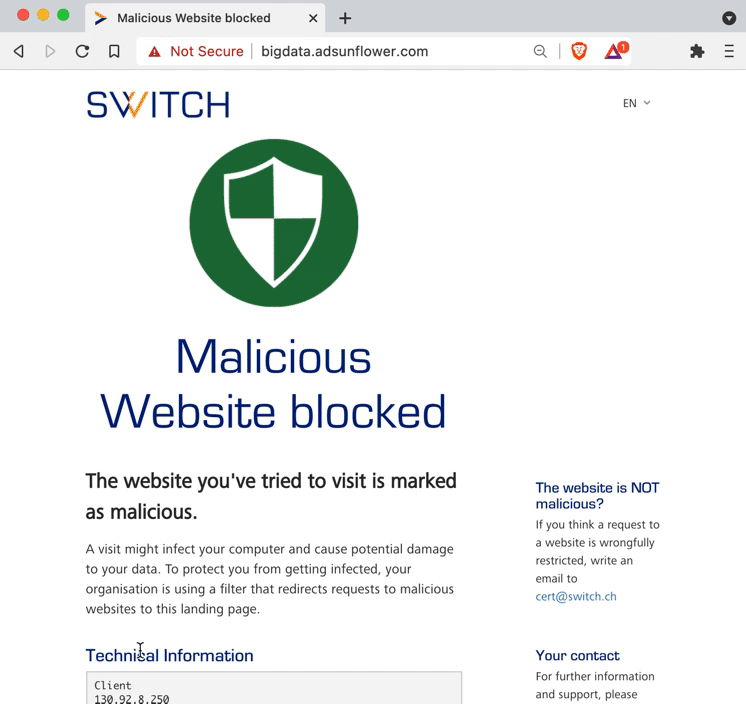
When redirecting to the information page, the web browser may show you a certificate warning. This happens when you want to visit a website identified as dangerous, which is encrypted using HTTPS. For HTTPS websites, the web browser checks whether the domain name (www.xyz.com) in the web browser's address bar matches the one in the certificate (required for encrypted communication). By redirecting to the information page, which is also secured with HTTPS, the domain name in the address bar remains the original one, but the domain name in the certificate changes to that of the information page (landingpage.mw.rpz.switch.ch).
Due to this difference, the web browser correctly suspects a fraud attempt and warns you about it. As you can see in the image below, by viewing the detailed information of the certificate warning, you can see that the DNS Firewall is involved.
When does the DNS Firewall not provide protection?
The DNS Firewall does not prevent receiving phishing emails or being infected with malware. The latter is the responsibility of the Antivirus program, and unfortunately, the receipt of phishing emails cannot be efficiently prevented so easily.
Since new and targeted phishing websites have a low profile at the beginning of their lifetime, it may take some time until the databases are updated, and the protection becomes effective.
Therefore, despite DNS Firewall, it is important to be attentive and cautious.